Pseudo-Proxy RAT CnC Architecture
2024-07-22 00:05:08
Zombie -> CnC <- Remote
Disclaimer
This article is for research purposes. If you replicate this, I will not be held responsible for any illegal activity.
Diagram
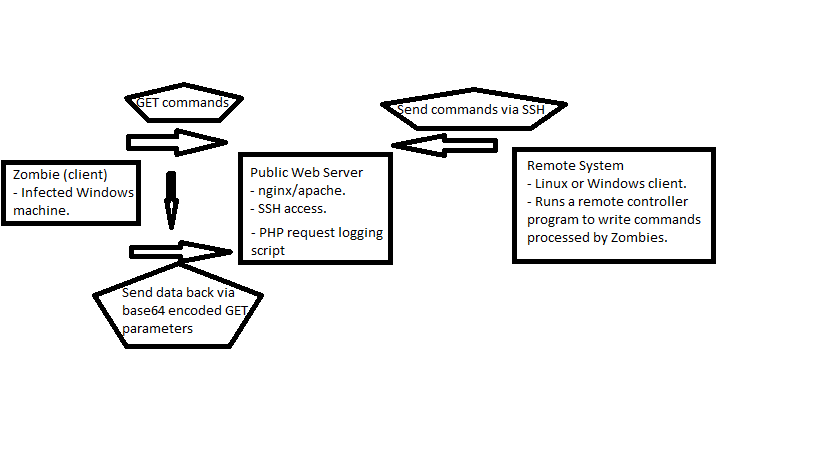
The zombie contains a RAT program that runs GET requests on specific pages hosted on a web server. These pages contain numbers, which execute different functions on the zombie, such as take a screenshot, run a command, or ping a hostname/IP address. The output from the screenshot and run command will be sent back to the source web server via URL parameters containing a base64 encoded string. Server side, the base64 encoded data is decoded and uploaded to the source filesystem after doing a few checks to ensure the file is valid and not corrupt.
Optimally, a Tor session should be created for each of the zombies upon the start of a session. These sessions should connect to the remote web server over a .onion domain.
The architecture zombie -> CnC <- remote is a useful way to implement a non-realtime alternative to the commonly misconfigured reverse TCP socket you saw back in the day. Those are extremely trackable, and this more isolated. A simple GET request vs a TCP socket is also likely to be less detectable in terms of network traffic, but I haven't proved that. Alternatively, you can add multiple domains that are checked one by one in case the main CnC domain goes down. You can also add a system to jump between multiple proxy SSH servers until getting to the final one in order to hide your source IP address.
Check out these notes...
